Who's Had More Vulns- PHP, Java, or ColdFusion?
Update: There's an updated blog post with more current results here:
http://www.codersrevolution.com/blog/whos-had-more-vulns-redux-php-java-coldfusion-ror-or-net
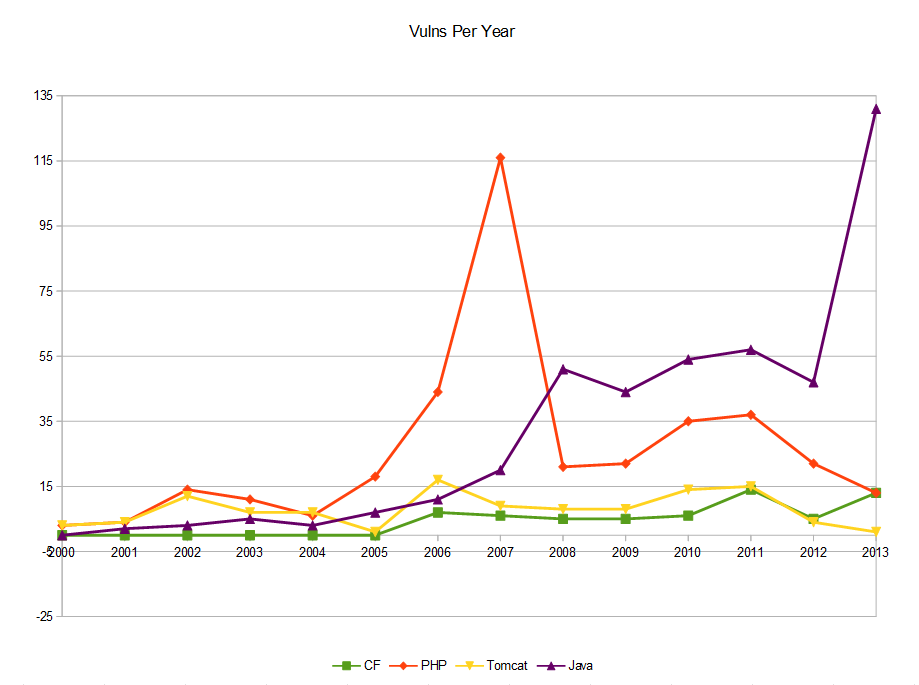
I get tired of people on complaining about ColdFusion as a technology choice because it's "so insecure". I regularly am told that it has more holes, more vulnerabilities, and a worse track record than other platforms. That's why I compiled this quick chart showing the number of Common Vulnerabilities and Exposures (CVE) by year for CF as well as PHP and Java (as reported by cvedetails.com) which are two of the most-used languages on the web. I also threw in Apache Tomcat for comparison since it completes in the web space and CF10 actually runs on a version of it.
So to break this down, the red line riding out on top with a huge spike in 2007, that's PHP. The purple line coming out of the backfield for a solid lead (?) at the end is Java. The yellow line is Tomcat who still manages 10-15 vulns a year (and the only one to go LOWER than CF. And that green line on the bottom with the lowest number of vulns every year, and nothing even reported until 2006- that would be CF.
So, sure-- there's a lot more info than just the counts on the chart. My point also isn't that PHP or Java are bad-- I'm just trying to make the point that oft-used technologies are targeted by crackers and nobody is perfect. And according to this data, CF is doing way better than several of the main techs out there. It should also be noted that CF, Java, and PHP were all created the same year-- 1995, so don't give me any of this "old" crap either. (Tomcat was created in 1999)
References:
- http://en.wikipedia.org/wiki/Timeline_of_programming_languages
- http://en.wikipedia.org/wiki/Apache_Tomcat
- http://www.cvedetails.com/vendor/74/PHP.html
- http://www.cvedetails.com/product/8739/Adobe-Coldfusion.html?vendor_id=53
- http://www.cvedetails.com/product/1526/SUN-JRE.html?vendor_id=5
- http://www.cvedetails.com/product/887/Apache-Tomcat.html?vendor_id=45
Tom Chiverton
And, of course, every Java or Tomcat issue is a potential CF vulnerability...
PS, you still have snow on your web site
Ron Stewart
With ACF running on top of Tomcat and Java, it seems a bit misleading to me to look at those three separately rather than as a unified stack. That's a key difference between ACF and PHP, for instance. This doesn't feel like a real apples-to-apples comparison.
Brad Wood
Yep, that's correct. No one ever tells me "CF is insecure because it runs on Tomcat", etc. The mindset I'm addressing is one where people feel ColdFusion is inherently a block of swiss cheese all on its own.
Regarding the snow-- yes I know. I don't know where you live, but it's still falling into single digits here in Kansas City every night and the forecast on my phone still has little snowflakes so I'm leaving the digital snow until I can finally wear shorts again. :)
Brad Wood
@Ron, I'd say we're looking at different ends of the apple. To be fair, I would have to also add in the vulns for Windows/Linux, and Apache/IIS/NginX, and all databases--- and let's not forget that PHP is written in C!
But that's not the point. I'm not trying to show the sum total of all vulns that may be present on your public-facing server. This is more of a snapshot of the inherent vulnerabilities produced by each vendor and their product.
While no one on Twitter complains to me that ColdFusion is written in Java or runs on Tomcat (at least from a security perspective), I regularly hear about Adobe's "bad track record", so this chart is also just as much about the quality of software that those 3 vendors put out. And in that case, it makes very much sense to keep them separated.
Ron Stewart
@Brad: You may not be seeing those complaints on Twitter, but I regularly deal with the perspective from the cybersecurity group where I work that ACF+Java have to be considered together. ACF can't be there w/o Java and ACF is in fact the only reason Java has to be installed on our servers. Regardless of underlying OS or outward-facing Web server, there is a difference in the middle layer. I agree there is some value in the comparison you've offered and I'm glad you dug out the data.
Pat Branley
Your problem with the Java vulnerabilities is that they relate to the JRE as a whole.
Most Java problems relate to applets, so its not a fair comparison. If you have Linux server with no X-windows installed, you cant run any applets so they shouldn't count right ?
Brad Wood
@Pat I would also argue that none of the CF 0-days last year applied to me because they were only exploitable if you had your web-based admin exposed or were using web sockets (neither of which apply to my servers).
The point though was the general track record of each technology and their vendor.
Maarten
Since the communities of the other compared languages is bigger than CF, wouldn't it be logical they get more vulnerabilities reported?
Brad Wood
@Maarten: Yes, that's a distinct possibility. I don't think it significantly changes the meaning of this data though.
People don't come to me and say, "CF in insecure due to the number of potential vulns that could be theoretically reported." Instead, I have people try to convince me that CF is already more insecure due to the current number of known vulns. This data, however proves otherwise as CF is shown to have far fewer actual known vulns on average.
Brad Wood
Here's a really nice write up on comparing security vulns and remediations in the most popular languages. It has some really good things to say about ColdFusion and how well it remediates vulnerabilities.
http://www.wmctv.com/story/25249464/whitehat-security-reveals-relative-security-of-web-programming-languages-in-2014-website-security-statistics-report